Validate access to SCP
Validate the SCP Access and add members to the team for Administration and Development activities.
- Login to SCP.
-
Under Overview, click Account Name.
Click New Account to create tenants such as Dev, QA, and PRD with SCP account.
-
Click on Tenant (sub account) to view the Services and validate
the settings.
Navigate to Members tab as shown below.
Figure 1. SCP Account Members 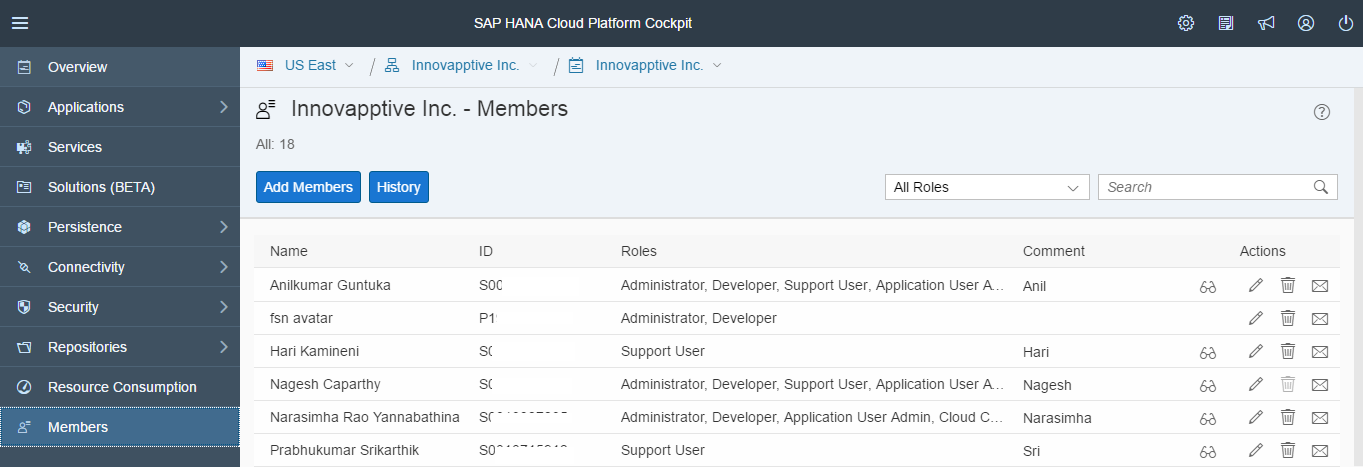
-
This tab helps you to add new members to the SCP Tenant. Use any of the
predefined roles for the new members that you add.
Table 1. Roles for SCP Tenant Members Role Description Administrator - Manages account members
- Creates new accounts using the self-service option
- Moves quota between accounts (prerequisite: user must be assigned an administrator role in each account)
- Manages subscriptions, trust, authorizations, and OAuth settings, and restart SAP HANA services on HANA databases.
- Has developer permissions, except debugging.
Note: This role grants permissions to view the Connectivity tab in the SAP Cloud Platform cockpit.Cloud Connector Admin Helps open secure tunnels via Cloud Connector from on-premise networks to cloud accounts.
Note: This role also grants permissions to view the Connectivity tab in the SAP Cloud Platform cockpit.Developer - Performs development tasks, such as deploying, starting, stopping, and debugging applications.
- Changes loggers and perform monitoring tasks, such as creating availability checks for applications and executing MBean operations.
Note: This role is assigned to a newly created user by default.Support User Accesses account data, including metadata, configuration settings, and log files. This role is assigned to technical support engineers.
Note: To read the database content, a database administrator must assign appropriate permissions to this role.Application User Admin - Manages user permissions on application level to access Java, HTML5 applications, and subscriptions.
- Controls permissions by assigning users to specific application roles or by assigning users to groups, which you then assign to application roles. Also unassigns users from roles or groups.
Note: Cannot manage account roles and perform actions on accounts. (for example, stopping or deleting applications).
